After the installation process is complete you'll be taken to the user interface, which is simple and easy to understand. Nine tabs run across the top the interface, one for each feature that Gecko monitors. Before using Gecko for the first time you can adjust the settings to suit you and can change things like the secret combination that re-opens the console and how often screenshots are taken, along with a ton of other settings.
Once you're ready to start monitoring you simply click the 'Start Monitoring' button and Gecko minimizes itself into silent mode. When hidden Gecko is completely undetectable and won't be found in the task manager, task bar or the add/remove programs window. The installation folder is also deep inside the Windows directory, so there's no chance of it being found.
While in silent mode, the software will monitor everything that goes on while you're away. Even after the computer is restarted. You can either have the logs emailed to you at set intervals (say once a day) or log back into the user console to look at the logs in detail.
When you log back into Gecko using your secret key combination you will be asked to enter your password. Once entered, you're presented with the home screen, which tells you how long Geckos been monitoring for and what exactly has been monitored. You can then click through each tab to see exactly what's been happening.
The next three tabs monitor all aspects of file and document use, which is perfect if you're monitoring an office environment. The first tab monitors all printed documents, along with time, date, name of document and name printer. The second tab monitors the clipboard, meaning anything copied and pasted will be reported here. The third tab monitors all file activity, meaning any file/document created, saved, opened or deleted will be reported here.
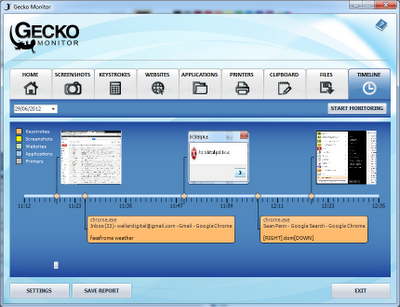
The final tab in Gecko Monitor is the 'Timeline' tab, which shows you an easy to flick through snapshot of everything that's happened during the chosen day. You can skim through the timeline and see screenshots and entered keystrokes, then click on the event to be taken to the corresponding tab.
Author Bio : John Jones, the writer of this article runs www.KeyloggerDownloads.com – a website that provides reviews of Phone Spy Software and Computer Monitoring Software.
If you wants to write the article, Kindly contact via contact form.
 If you enjoyed this post and wish to be informed whenever a new post is published, then make sure you subscribe to my regular Email Updates.
Subscribe Now!
If you enjoyed this post and wish to be informed whenever a new post is published, then make sure you subscribe to my regular Email Updates.
Subscribe Now!
Click Here To Download Winspy Keylogger