Filed Under: MISCELLANEOUS
Sunday, December 22, 2013
Excellent YouTube Video Downloader from iSkysoft
Excellent YouTube Video Downloader from iSkysoft
2013-12-22T23:23:00-08:00
wildrank
MISCELLANEOUS
|
Comments
Posted by
wildrank
on
Sunday, December 22, 2013
If you are not happy with your current internet connection speed and those annoying pop-ups that come over your computer screen then you must do one thing and that is to download the iSkysoft Free Video Downloader.
There are many times when you log on to YouTube and want to watch your favorite videos but due to slow internet connection speed and annoying pop-ups you close your computer. With the help of iSkysoft Free Video Downloader you can download all those videos on your computer on the hard-drive and watch them later when you are free. Another best part about this software is that it offers smooth and error free download.
Filed Under: MISCELLANEOUS
Friday, November 29, 2013
Beef Up The Security In Your Home Office With 5 Great Pieces Of Software
Beef Up The Security In Your Home Office With 5 Great Pieces Of Software
2013-11-29T10:47:00-08:00
wildrank
MISCELLANEOUS
|
Comments
Posted by
wildrank
on
Friday, November 29, 2013
More people work from a home office these days which means they don't have an IT team to help keep them safe, so I've talked about some software they can use instead.
Are you one of those people who are now running your business from a home office? It must feel good sleeping about 10 meters away from your place of work, but it's not all rosy because security is still an important issue. We're going to look at some software you can use to beef up the security inside your home office so your business will always be safe.

Filed Under: MISCELLANEOUS
Saturday, November 16, 2013
How to Block Unwanted Emails
How to Block Unwanted Emails
2013-11-16T10:54:00-08:00
wildrank
HOW STUFFS WORK
|
Comments
Posted by
wildrank
on
Saturday, November 16, 2013
Unsolicited emails or spam emails are big annoyances to email users in the world. In case if your email address falls into the wrong hands, it can be sold and resold to many marketers in the world who tend to flood email addresses with various different kinds of ads, irrelevant requests for money, product review and other types of spam. It can be vary irritating for email users.
Most E-mail accounts come with an automatic junk mail filter, but even these don't catch all kinds of unsolicited emails. Thats why you need to manually block unwanted emails.

Filed Under: HOW STUFFS WORK
Sunday, November 10, 2013
Startapp : Checkout The Site To Know How To Make Profits By Developing Android Apps
Startapp : Checkout The Site To Know How To Make Profits By Developing Android Apps
2013-11-10T05:39:00-08:00
wildrank
MISCELLANEOUS
|
Comments
Posted by
wildrank
on
Sunday, November 10, 2013

Are you an app developer and want to launch a new Android application? And really want to know how to make money from the app development than check out Android news. Through this method, you come across the latest trend and you will find that people are crazy about android apps and devices. This is proved by the increasing demand of the applications and Android phones. This is not the case of one or two nations, but the whole world wants to go Android.
Filed Under: MISCELLANEOUS
Thursday, November 7, 2013
5 Technologies You'll Need To Hack Google's Search Engine Algorithm
5 Technologies You'll Need To Hack Google's Search Engine Algorithm
2013-11-07T23:35:00-08:00
wildrank
MISCELLANEOUS
|
Comments
Posted by
wildrank
on
Thursday, November 07, 2013
Making money from a website is easy if you have a lot of traffic, so I've talked about things people can use to hack the search engine algorithm in order to get first-page rankings. Building a profitable website doesn't need to be hard if you know what you're doing. At the end of the day you could easily copy the ways more successful people are making money and some of those pennies would fall into your wallet. Your biggest problem is going to be getting traffic because without it you won't be able to make anything. It's actually not too hard to get tons of traffic if you're creative, but it will involve hacking the search engine algorithm.

Filed Under: MISCELLANEOUS
Tuesday, October 29, 2013
4 Easy Ways To Stop Phone Hackers Snooping Through Your Dirty Laundry
4 Easy Ways To Stop Phone Hackers Snooping Through Your Dirty Laundry
2013-10-29T11:52:00-07:00
wildrank
MOBILE HACKS
|
Comments
Posted by
wildrank
on
Tuesday, October 29, 2013

Most people are never going to have their phone hacked, but it will happen to some of us which is why we all must be prepared. I've spoken about a few simple ways people can protect themselves.
I bet you can't even remember the last time you left home without your smartphone unless it was by accident. That is a testament to how popular they've become and there are definitely an integral part of our lives, but with great power also comes great danger. At the end of the day your handset is still just an electronic device and it can be hacked into if you're not careful.
If you keep up with worldly news you've probably heard about what happened in the UK, where a newspaper took it upon itself to hack into its citizens phones. If massive organizations are doing it you don't even want to imagine who else could be trying to exploit you at any time of the day. We're going to take a look at some of the best things you can do to keep your phone safe from hackers.
Filed Under: MOBILE HACKS
Sunday, October 27, 2013
How To Keep Hackers Out Of Your Precious WordPress Site
How To Keep Hackers Out Of Your Precious WordPress Site
2013-10-27T03:16:00-07:00
wildrank
MISCELLANEOUS
|
Comments
Posted by
wildrank
on
Sunday, October 27, 2013

WordPress is a great platform to use when building a business, but if people are not careful they could end up in trouble. I've talked about a few ways they can keep hackers out of their site.
If you run a WordPress blog you have reason to worry because there are hackers floating around looking to expose the weaknesses of people like you. If people can break into government networks it's obvious they will be able to hack into your site, but luckily you don't need to let that bother you. All the amazing hackers won't care one little bit about your insignificant blog because you're just small fish.
That being said, there are still millions of semi-skilled hackers who want to cause as much destruction as possible and your website is fair game. Because they won't be targeting you directly it's easy to stay out of their path by making sure you're following a few things. Take a look at what they are and implement them as soon as possible if you've neglected to do it so far.
Filed Under: MISCELLANEOUS
Friday, October 25, 2013
Ultimate Virus Builder - Create Your Virus In Seconds
Ultimate Virus Builder - Create Your Virus In Seconds
2013-10-25T12:09:00-07:00
wildrank
HACKING SOFTWARES
|
Comments
Posted by
wildrank
on
Friday, October 25, 2013
Today in this article I am going to share one more virus creator software, few months back I had shared Atomic Virus Creator software for same purpose. In this tutorial I am going to teach you how to create customize virus using Ultimate Virus Builder software. Ultimate Virus Builder offers you more than 50 options to customize your virus. In this software you can set any icon for your virus ! Not only does this tool allow you to create own customize virusses, it can also help you spoof the extension of any file with the built in extension spoofer ! This Ultimate Virus Builder has an automatic update feature, so you'll never have to worry about downloading the latest version.

Filed Under: HACKING SOFTWARES
Friday, October 18, 2013
A Little Bit of Information About Image Captcha
A Little Bit of Information About Image Captcha
2013-10-18T11:59:00-07:00
wildrank
MISCELLANEOUS
|
Comments
Posted by
wildrank
on
Friday, October 18, 2013
This article explains how captcha works, why it's necessary and where it comes from - and provides a lot of interesting facts along the way.

A Little Bit of Information About Image Captcha :
If you have ever attempted and failed to log into an e-mail account or any other online account, then you will probably have encountered image captcha at some point. That's the technical term for the little box of unusual looking text that crops up and asks you to type what you see. Sometimes it will come up when you've entered an incorrect password a few times, other times it will appear as soon as you try and enter any data into a form. But what precisely is captcha, why does it exist? And what does it have to do with hacking?
Filed Under: MISCELLANEOUS
Tuesday, October 15, 2013
The Oracle Cloud Application Exam for Implementation Specialist Certification
The Oracle Cloud Application Exam for Implementation Specialist Certification
2013-10-15T07:30:00-07:00
wildrank
MISCELLANEOUS
|
Comments
Posted by
wildrank
on
Tuesday, October 15, 2013

Sales professionals and technical IT staff involved in the implementation of Oracle Cloud Application Technologies can achieve professional certification as an Implementation Specialist, or as an OPN Specialist, if working for an Oracle Partner Network member organization. To earn your certification, you need only pass one Oracle certification exam, the 1Z0-468. This test, which is formally titled the Oracle Cloud Application Foundation Essentials, is comprised of 76 questions in several major topic areas related to the selling and implementation of Oracle Cloud Application Foundation solutions. Included in the topics that appear on the exam are WebLogic Server, Oracle Virtual Assembly Builder, and Java SE, among many others.
Filed Under: MISCELLANEOUS
Wednesday, October 2, 2013
Free Download Internet Download Manager 6.17 Full Version
Free Download Internet Download Manager 6.17 Full Version
2013-10-02T11:59:00-07:00
wildrank
hack IDM
|
Comments
Posted by
wildrank
on
Wednesday, October 02, 2013

IDM or Internet Download Manager is a Well known and popular software used by Millions of people through out the world For downloading Data At high Speeds From the Internet . It is a 3rd party replacement for your Browser's default download Manager . Upon installation it automatically installs a plugin in your web Browser which enables it to takeover all the downloads from that Moment onward .
Internet Download Manager can help you accelerate your downloads. It works by creating various threats so that multiple sections (up to 16) of the same file can be downloaded at the same time. In addition, it lets you pause and resume your downloads, an action that is not always available from regular procedures.
Internet Download Manager is a powerful download software. Its a most popular in the world .IDM is a tool to increase download speed, pause and resume or schedule download.It can resume broken connection .IDM support proxy server, fttp and http protocols. IDM integrates seamlessly into Microsoft Internet Explorer, Netscape, MSN Explorer, AOL, Opera, Mozilla, Mozilla Firefox, Mozilla Fire-bird, Avant Browser, MyIE2, and all other popular browsers to automatically handle your downloads.
Filed Under: hack IDM
Monday, September 23, 2013
How To Setup Port Forwarding Using Software
How To Setup Port Forwarding Using Software
2013-09-23T13:08:00-07:00
wildrank
Port Forwarding
|
RATS
|
Comments
Posted by
wildrank
on
Monday, September 23, 2013

Hie Guys, After long break I am going to write one more article on port forwarding which is required in setting up RAT softwares. In past I have wrote two article on port forwarding - one of them is manual port forwarding and second one is using Utorrent. But in Utorrent at a time you can't forward more than one port and that manual port forwarding is quite difficult for non technical persons. So today in this article I am going to share one software which you can use for forwarding more than one port at a time.
For connecting to your remote victim, you should have your port forwarded. You can setup port forwarding using default router panel. But, every router has different options making it complicated. Hence, the best way to setup port forwarding using software. So, In this article I am posting on "how to setup port forwarding using Port Forwarding software ".
Filed Under: Port Forwarding , RATS
Sunday, September 15, 2013
Cellphone Hacking | Review For Top Two Cell Phone Spy software
Cellphone Hacking | Review For Top Two Cell Phone Spy software
2013-09-15T10:40:00-07:00
wildrank
MOBILE HACKS
|
Comments
Posted by
wildrank
on
Sunday, September 15, 2013
Yet I have shared two cellphone hacking or spying software on wildhacker(WH) - first Mobile spy and second one is SpyBubble which you can use for monitoring your spouse mobile activities. Means you can use it this mobile hacking software to monitor children or monitor employees or girlfriend or boyfriend daily activities. Such cellphone spying sofware can silently record every SMS and information about each call and message. You can also see GPS positions every thirty minutes. For receiving such information you just need to do is install a good cell phone spy software on the target cell phone.
But today there are lots of mobile spying or hacking software are available on internet, so its difficult for peoples to make the right choice so as to fit their spying needs. So, in order to help our readers to find the best spy software, I have decided to give a thorough review of the Top 2 Best Selling SpyPhone softwares on the market.
Filed Under: MOBILE HACKS
Vine for Android is Renewed with Interesting New Features
Vine for Android is Renewed with Interesting New Features
2013-09-15T10:38:00-07:00
wildrank
MISCELLANEOUS
|
Comments
Posted by
wildrank
on
Sunday, September 15, 2013

Just when you thought Instragram couldn’t get any better, a brand new app appears to steal the stage. Twitter’s six-second mobile looping vide-sharing mobile app, Vine has recently been released for Android phones. This means that Android users no longer have to share dirty looks with iPhone users. As a matter of fact, Vine for Android seems to offer the exact same features that it offers to iOS phones, so this is great news.
Filed Under: MISCELLANEOUS
Saturday, September 14, 2013
The End Of SEO? How Optimistic Can You Get After Being Struck By The Penguin?
The End Of SEO? How Optimistic Can You Get After Being Struck By The Penguin?
2013-09-14T09:55:00-07:00
wildrank
MISCELLANEOUS
|
Comments
Posted by
wildrank
on
Saturday, September 14, 2013

In the world of search engine optimization, the effects of the mighty Google Penguin ravishing everything in its path are being felt harder and harder, as after the first shock, mass hysteria, the questions and the explanations, finally the skies got clear, the dust descended to the ground and all there is left are some ruins to contemplate. Or this is how Brian Case from exploreb2b.com feels when asked on his views on the future of SEO.
Filed Under: MISCELLANEOUS
Wednesday, September 11, 2013
How to Send Spoofed Emails Anonymously | Fake Mailer
How to Send Spoofed Emails Anonymously | Fake Mailer
2013-09-11T11:10:00-07:00
wildrank
KEYLOGGER
|
Phishing
|
Comments
Posted by
wildrank
on
Wednesday, September 11, 2013

Hi guys! I am back with another amazing and mind blowing tutorials for my reader. In this tutorial I am going to explain you how to send an anonymous email to someone. You must be thinking what is the purpose to send an anonymous email, I will be explaining that too in this detailed post.
What is Email Spoofing?
Email Spoofing is a process of faking source address of an Email. It means that we can show that email has been sent from someone else. This could be quite useful in various client side hacking techniques and is an important part of Social Engineering. Using Email Spoofing techniques you can send fake emails to users to win their trust in order to execute our attack. Since the source address will be fake(Probably a mail from some famous trusted company) our victim will believe the mail and will be hacked.
Filed Under: KEYLOGGER , Phishing
Tuesday, September 10, 2013
Hack Facebook Twitter Account Password Using Spy Keyloggers
Hack Facebook Twitter Account Password Using Spy Keyloggers
2013-09-10T07:25:00-07:00
wildrank
antikeylogger
|
KEYLOGGER
|
MOBILE HACKS
|
Comments
Posted by
wildrank
on
Tuesday, September 10, 2013
Now days using computer or phone is not safe because their are lots of software / tool available all over internet in the world that aim to destroy or distract the computer / phone users. These tools are mainly used for stealing important information of users like username password of email accounts, bank information etc.
These hacking tools are keylogger, cell phone spy software, iStealer etc. By using these all software you can easily monitors your computer and others computer also. Some peoples use it for legal purpose, some use these type of tools for illegal purpose. Some user used such keylogger or spy software to hack others valuable information like account password etc. But you can protect your computer or cell phone from such computer using some antivirus like Nortan Antivirus or using anti keylogger like SpyShelter
Using such types of keyloggers or cell phone spy software you can monitors not only you computer or phone but can also monitor other computer or phone which is connected to internet. These remote installation, monitoring feature is helpfull to monitor your Spouse activities or to hack your victim email account password etc.
Filed Under: antikeylogger , KEYLOGGER , MOBILE HACKS
Sunday, September 8, 2013
How To Spy Mobile Phone Calls SMS Conversation
How To Spy Mobile Phone Calls SMS Conversation
2013-09-08T10:50:00-07:00
wildrank
MOBILE HACKS
|
Comments
Posted by
wildrank
on
Sunday, September 08, 2013

mSpy is a background smartphone application that secretly records and logs SMS messages, Call history, calendar tasks and memos; bugs meeting rooms or whatever surroundings; tracks GPS locations of the phone in real time and displays all routes on a convenient map. The software installs directly into the phone you wish to monitor. However, physical access to the device is only needed for initial download. All settings may be adjusted remotely anytime online right from your web Control Panel. After the installation process is completed, as soon as in 20 minutes, all data, even those deleted, are uploaded to your private Control Panel account which is available from any PC or phone browser.
Filed Under: MOBILE HACKS
Wednesday, September 4, 2013
Rolling the Dice on Casino Stocks – Stopping Hackers Cited for the Increase
Rolling the Dice on Casino Stocks – Stopping Hackers Cited for the Increase
2013-09-04T11:25:00-07:00
wildrank
MISCELLANEOUS
|
Comments
Posted by
wildrank
on
Wednesday, September 04, 2013

If you have stocks in casinos, you should be smiling right now as they are up again this year. One of the main things the casinos have been trying to gain a good foothold in this year is stopping people attempting to hack and game the gaming houses.
This is forcing the profits even higher.
If you haven’t dabbled in this stock, well read on and see for yourself if you fancy your chances gambling on casino stocks.
Although you often hear the phrase, “The house always wins” in the gambling world, buying casino stocks can bring you big long-term profits. Just as you would with any investments, it is wise to heavily research the subject and choose wisely.
Although these stocks possess a degree of predictability, the net income growth rates are anything but – they depend wholly on the economy.
Filed Under: MISCELLANEOUS
Sunday, September 1, 2013
Hack Website : Basic Information About Website Hacking Part 1
Hack Website : Basic Information About Website Hacking Part 1
2013-09-01T12:12:00-07:00
wildrank
Website Hacking
|
Comments
Posted by
wildrank
on
Sunday, September 01, 2013

Well I have posted lots of articles on Email Hacking which includes Phishing and keylogging etc, but today I would like to throw some light on new topic which is "Website Hacking". Today i am first time writing article on "Website Hacking". why I am writing this article as there are lots of newbies having lots of misconceptions related hacking website, So I hope this tutorial cover all those misconception and if not all most of them.
Website security is a major problem today and should be a priority in any organization or a webmaster, Now a days Hackers are concentrating alot of their efforts to find holes in a web application, If you are a website owner and having a High Page rank and High Traffic then there is a chance that you might be a victim of these Hackers.
Filed Under: Website Hacking
Monday, August 19, 2013
CEO Mark Zuckerberg’s Facebook Wall Hacked
CEO Mark Zuckerberg’s Facebook Wall Hacked
2013-08-19T03:54:00-07:00
wildrank
MISCELLANEOUS
|
Comments
Posted by
wildrank
on
Monday, August 19, 2013

Khalil, a Palestinian white hat hacker, submitted bug reports to Facebook about a vulnerability that allowed him to post on anyone's wall. But Facebook's security team didn't do anything. So Khalil wrote on Mark Zuckerberg's wall about it and was generally a badass.
Filed Under: MISCELLANEOUS
Monday, August 12, 2013
Hack Website Admin Account | Basic SQL Injection Attack
Hack Website Admin Account | Basic SQL Injection Attack
2013-08-12T12:20:00-07:00
wildrank
Website Hacking
|
Comments
Posted by
wildrank
on
Monday, August 12, 2013
Hello everyone!! Previously we have discussed many website hacking tutorial on WildHacker. Today,I am going to tell about one more very usefull but old method which you can used to hack website using Basic SQL Injection Attack. We're gonna hack into an admin account, using SQL injections. How does it work?? A SQL injection injects a code into the MYSQL database which gets passed the site security login.

Filed Under: Website Hacking
Friday, August 9, 2013
7 Poker Apps I Simply Can’t Get Enough Of
7 Poker Apps I Simply Can’t Get Enough Of
2013-08-09T10:52:00-07:00
wildrank
In the ever growing world of technology, I’m going to give you a list of the best 10 poker apps. Some of them are classics while a few of the games are really beginning to push the boundary. Be sure to get some of these wonderful games on your smart phone, because if you’re anything like me, I can promise you won’t be able to put your device down!
Live Holdem Poker Pro
Live Holdem Poker has quickly become the 1 app in the android store. A very social game that allows to go for the big pot against either your friends or one of the millions of social players. The slick design gives the feel of that real, tense poker game added with the ability to psych out in the chat section makes this game my favourite in the app store.
Sunday, August 4, 2013
How To Hack Mobile Phone Using mSpy Mobile Keylogger
How To Hack Mobile Phone Using mSpy Mobile Keylogger
2013-08-04T12:15:00-07:00
wildrank
MOBILE HACKS
|
Comments
Posted by
wildrank
on
Sunday, August 04, 2013

Are You Looking for the best Cell Phone Spy software . Look no further than mSpy spyware for cell phones mSpy cell spy software leverages the latest developments in cell spy technology to give you an inside look at what’s really going on. No more worries and no more uncertainty - just the facts. mSpy is compatible with jail-broken iPhones, Android, Symbian and BlackBerry operating systems.
Filed Under: MOBILE HACKS
Tuesday, July 30, 2013
FUD Crypter Aug 2013 Free Download - Bypass Antivirus Detection
FUD Crypter Aug 2013 Free Download - Bypass Antivirus Detection
2013-07-30T11:31:00-07:00
wildrank
CRYPTER
|
Comments
Posted by
wildrank
on
Tuesday, July 30, 2013

Yet I have written many articles on Keyloggers, Rats and iStealer which you can use to hack victims email account passwords, But the problem is that this such hacking tools can be easily detected by victims antiviruses. So to bypass antivirus detection we have to crypt our Keyloggers, Rats and iStealer server file using a Crypter. As said above, Crypter is free software tool used to hide our viruses, RATs or any keylogger from antiviruses so that they are not detected and deleted by antiviruses. Thus, a crypter is a program that allow users to crypt the source code of their program. Generally, antivirus work by splitting source code of application and then search for certain string within source code. If antivirus detects any certain malicious strings, it either stops scan or deletes the file as virus from system.
Filed Under: CRYPTER
Sunday, July 28, 2013
All Premium Download Link Generators 2013
All Premium Download Link Generators 2013
2013-07-28T11:32:00-07:00
wildrank
Premium Downloading
|
Comments
Posted by
wildrank
on
Sunday, July 28, 2013
Hi all fans, today we're here to introduce a new working premium link generator site for Rapidshare, turbobit.net, Bayfiles, Mediafire, Netload.in, Extabit, Ul.to, Freakshare and for many more sites. As most of the file sharing sites set some kind of restrictions for Free users like free users cannot use download managers for downloading file, cannot resume broken downloads,cannot pause the downloads and free users have to wait long times for file download. It’s even more impossible to download from a lot of these file host sites “rapidshare, upload.to, rapidgator, ryushare, extabit , etc. as a free user, which these uploaders are hosting their files to.

Filed Under: Premium Downloading
Friday, July 26, 2013
Why You Should Consider a Career in Cybersecurity
Why You Should Consider a Career in Cybersecurity
2013-07-26T05:22:00-07:00
wildrank
MISCELLANEOUS
|
Comments
Posted by
wildrank
on
Friday, July 26, 2013

In some metropolitan areas, the U.S. is already facing a major IT personnel shortage. That claim may sound odd when you're constantly hearing news about IT job cuts. For example, the Washington Post recently reported that since Q1 2013, the business world announced a 144-percent increase in IT job cuts. However, the U.S. economy produced nearly 10,000 more IT jobs this June than it did in June 2012.
If we need IT professionals so much, then why are we laying them off?The IT job market isn't shrinking, but the in-demand segments have changed. Big data, cloud computing, healthcare IT and mobile are growing while segments like hardware manufacturing are shrinking. To find out more about earning an IT degree that will actually take you places, click here for info. An online cybersecurity bachelor’s degree is one of the best degrees you can get right now.
Filed Under: MISCELLANEOUS
Thursday, July 25, 2013
Convert video files to mp4 for iPad
Convert video files to mp4 for iPad
2013-07-25T10:34:00-07:00
wildrank
Ipad
|
unlock iphone
|
Comments
Posted by
wildrank
on
Thursday, July 25, 2013

The major video file we will be talking about here is AVI. Due to the poor compression of AVI video files, these files are quite large. Most of the people need to convert the AVI video files to some other formats, most probably mp4 to play the video in good quality and avoid unbalanced pixels. Our focus in this article is to help you with conversion of AVI video files to mp4 format which can be easily played on various Apple devices like iPhone, iPad, and windows phones.
Filed Under: Ipad , unlock iphone
Wednesday, July 24, 2013
How To Bypass Mobile Phone Verification
How To Bypass Mobile Phone Verification
2013-07-24T11:20:00-07:00
wildrank
MISCELLANEOUS
|
Comments
Posted by
wildrank
on
Wednesday, July 24, 2013
Today in this article I'll introduce you to some websites which offering phone free numbers, which could be used for receiving SMS online for free. Most of the time we might not always be interested in providing our real personal phone numbers for SMS verification, or the country we reside in might not be supported by the site asking for verification, so in such cases we can bypass the verification step with the help of these kind of sites.

Filed Under: MISCELLANEOUS
Saturday, July 13, 2013
How To Hide Keylogger Server Files In a JPG Format
How To Hide Keylogger Server Files In a JPG Format
2013-07-13T12:32:00-07:00
wildrank
UNDETECTION TECHNIQUES
|
Comments
Posted by
wildrank
on
Saturday, July 13, 2013
Yet I have published so many articles on Keylogger like Ardamax, Winspy, sniperspy keylogger, in those article I have explained about how to create server file for hacking your victim computer. But If you send that .exe file directly to your victim, might be he / she will not run it. So today in this article I am going to show you how to hide keylogger server file under JPG image format.

Filed Under: UNDETECTION TECHNIQUES
Thursday, July 11, 2013
Malicious Pinterest browser plugin stealing passwords and spreading spam
Malicious Pinterest browser plugin stealing passwords and spreading spam
2013-07-11T12:15:00-07:00
wildrank
MISCELLANEOUS
|
Comments
Posted by
wildrank
on
Thursday, July 11, 2013

Social networking sites are unfortunately now major interest to malicious cyber criminals, spreading malware and building botnet army to steal money direct from your keyboards.
Filed Under: MISCELLANEOUS
Monday, July 8, 2013
Recover / Hack Gmail, Twitter Password Using Keylogger via Online Web URL
Recover / Hack Gmail, Twitter Password Using Keylogger via Online Web URL
2013-07-08T11:19:00-07:00
wildrank
KEYLOGGER
|
Comments
Posted by
wildrank
on
Monday, July 08, 2013

Now days this is one of the most frequently asked question via email or facebook fan page- "How To Hack Facebook Password". By the way I have already written so many article on facebook hacking like using Winspy keylogger / Sniperspy keylogger / Tabnabbing technique etc but today in this article I am going to share something different and easy technique. Many visitors also asked me about " How to install keylogger via url / link and hack the password ?? " So here is trick to Hack Facebook Password using script and FUD keylogger.
In this trick first you need to create keylogger file and have to share it on facebook profile, when someone click on that link and install that application(keylogger), Keylogger will start monitoring and will send all capture details on your email ID.
Filed Under: KEYLOGGER
Monday, July 1, 2013
Navigating Youtube's ‘ONE CHANNEL’ Format
Navigating Youtube's ‘ONE CHANNEL’ Format
2013-07-01T10:47:00-07:00
wildrank
hack youtube
|
Comments
Posted by
wildrank
on
Monday, July 01, 2013

In March 2013, YouTube rolled out its “One Channel” format with a new look and features that let you personalize your viewing experience. The new features serve two man purposes: first, they help you find interesting YouTube content based on your viewing habits and preferences, and second, they give visitors to your channel a clear idea of who you are and make it easier for them to subscribe. Navigating the One Channel format may seem confusing at first, so let’s take a look at some of the basics.
Filed Under: hack youtube
Thursday, June 27, 2013
Hack Facebook Account Password with just a text message
Hack Facebook Account Password with just a text message
2013-06-27T13:01:00-07:00
wildrank
hack facebook
|
Comments
Posted by
wildrank
on
Thursday, June 27, 2013

Can you ever imagine that a single text message is enough to hack any Facebook account without user interaction or without using any other malicious stuff like Trojans, phishing, keylogger etc. ? Today we are going to explain you that how a UK based Security Researcher, "fin1te" is able to hack any Facebook account within a minute by doing one SMS.
Because 90% of us are Facebook user too, so we know that there is an option of linking your mobile number with your account, which allows you to receive Facebook account updates via SMS directly to your mobile and also you can login into your account using that linked number rather than your email address or username. According to hacker, the loophole was in phone number linking process, or in technical terms, at file /ajax/settings/mobile/confirm_phone.php
Filed Under: hack facebook
Tuesday, June 25, 2013
Trace your girlfriends or friends mobile live for free instantly
Trace your girlfriends or friends mobile live for free instantly
2013-06-25T11:56:00-07:00
wildrank
MOBILE HACKS
|
Comments
Posted by
wildrank
on
Tuesday, June 25, 2013
Hello Friends, after my previous article on SMS hack today i am back with an one more awesome trick with you all. Today i will tell you how to hack mobile to track trace anyones mobile without gps with gps for free ,trace wife girl friend child hack trace
TRACE ANYONES MOBILE INSTANTLY WITH GPS AND WITHOUT GPS FOR FREE
Yes Guys, this is now possible...I m not jokingMany of us think that this is not possible or we have to spend some money for such services but believe me that we don’t have to spend any money for getting this done. Yes, PhoneOnMap makes it possible, which provides a free application that has to be installed in GPS cell phone and you are ready to track the phone from anywhere on the Internet.
Filed Under: MOBILE HACKS
Saturday, June 22, 2013
how to provide a full solution to your clients
how to provide a full solution to your clients
2013-06-22T00:07:00-07:00
wildrank
MISCELLANEOUS
|
Comments
Posted by
wildrank
on
Saturday, June 22, 2013

With the increasing trend of growing website solutions, the designers need to provide the best web solutions to their customers. IMcreator.com is one of such web solution organization that will provide such good web solutions to us. In this article you will learn about what are the features of good web solutions and how IMcreator.com is helpful in providing them.
Filed Under: MISCELLANEOUS
Monday, June 17, 2013
Website Hacking Part 3 : How to Hack websites using cross-site scripting (XSS)
Website Hacking Part 3 : How to Hack websites using cross-site scripting (XSS)
2013-06-17T11:45:00-07:00
wildrank
Website Hacking
|
Comments
Posted by
wildrank
on
Monday, June 17, 2013

As we had discussed about How to find a vulnerable Website? and Basic information of website hacking in my previous two article on wildhacker. Today i am writing this Part3 article on "Basic XSS Tutorial For Website Hacking". Today in this article, I am going to teach you how to hack website using XSS. In this article i have shared Cookie Catcher page, which is used for catching cookies.
Filed Under: Website Hacking
Sunday, June 16, 2013
How To Hack Gmail / YouTube Account Password
How To Hack Gmail / YouTube Account Password
2013-06-16T07:36:00-07:00
wildrank
HACK GMAIL
|
hack youtube
|
KEYLOGGER
|
Comments
Posted by
wildrank
on
Sunday, June 16, 2013
Gmail / YouTube is one of the most widely used site with millions of users. YouTube is undoubtedly the most preferred website to share and watch favorite videos. As a reason if which it has become the number 1 target of hackers, I have written a couple of post related to gmail and youtube hacking, But here in this article I am sharing top methods on how hackers can hack Gmail / YouTube accounts in 2013
Today in this article I am going to share some of hackers favorite method which you can also used to hacked Gmail and Youtube account password of your victim accounts.
Filed Under: HACK GMAIL , hack youtube , KEYLOGGER
Friday, June 14, 2013
Complete HACKING information for Newbies
Complete HACKING information for Newbies
2013-06-14T11:53:00-07:00
wildrank
Basic Hacking
|
Comments
Posted by
wildrank
on
Friday, June 14, 2013

I saw many peoples who just wants to hack someone email account password or computer but dont know "How To Hack It??". So normally they search about it in google and google shows long list of search result. After that they pickup any one of it and follow the tutorial, but the problem is all such tutorial are not safe. It can also hack your account password too instead of your victim password. So be aware of it and follow only trusted website tutorials. I saw many of my site readers dont know basic information of hacking, So today I have decided to write such tutorial for all my newbies visitors who dont know basic things about hacking..
Filed Under: Basic Hacking
Sunday, June 9, 2013
Make Keylogger 100% FUD | How To Bypass Antivirus Detection
Make Keylogger 100% FUD | How To Bypass Antivirus Detection
2013-06-09T12:21:00-07:00
wildrank
CRYPTER
|
CRYPTOGRAPHY
|
Comments
Posted by
wildrank
on
Sunday, June 09, 2013
On WildHacker, I have written so many tutorials on Keylogger, iStealer, Rats hacking tool. But the main problem is antivirus detection, most of the hacking tools are dectable. So to bypass antivirus detection we have to make that server file ( which is created using Keylogger, iStealer, Rats ) fully undectable. Few months back I had already explained you Hexing tutorial to make such virus file or server file fully undectable. Today in this tutorial i am going to explain one more way to make virus file undectable using BackTrack. Antivirus protects machines from malware, but not all of it. There are ways to pack malware to make it harder to detect. We'll use metasploit to render malware completely invisible to antivirus. So follow the step by step instruction to make a virus Fully Undetectable from all the antiviruses.
Filed Under: CRYPTER , CRYPTOGRAPHY
Saturday, June 8, 2013
Mobile Hacking : Advantages Of Mobile Spy Technology On Smart Phones
Mobile Hacking : Advantages Of Mobile Spy Technology On Smart Phones
2013-06-08T10:19:00-07:00
wildrank
MOBILE HACKS
|
Comments
Posted by
wildrank
on
Saturday, June 08, 2013
Advantages of Mobile Spy technology on smartphones :
Smartphones are the technology gadgets that play a vital role in the lives of many people across the world. Most parents are skeptical about providing smartphones for their children with the fear that their children might misuse the cell phones. Children usually do not handle the cell phones as they are supposed to do. As a result, they end up being in trouble. However, with the help of Mobile Spy technology, one can ensure the safety and well being of one’s child and loved ones. Some of the major advantages of Mobile Spy technology have been listed below.
Best Monitoring Technology : Mobile spy is one of the major advancements in the smartphones technologies, which is helpful for the concerned parents to keep a tab on their children's cell phones. . It is an award winning smartphone monitoring application that was featured on media channels like PC World, Forbes, and CNN. Mobile Spy helps parents to track their children’s smartphone activities in a discreet manner. Your children would be clueless about the software that has been installed on their phones. Also, you can monitor on any cell phones that you own, such as the smartphone that you presented to your spouse or the one that you have allotted to your employee for official usage, thus to know if they are cheating on you in any aspect or if they are misusing their cell phone privileges.
Filed Under: MOBILE HACKS
Thursday, June 6, 2013
Hack Facebook Password | Email Password : Email Hacking
Hack Facebook Password | Email Password : Email Hacking
2013-06-06T12:28:00-07:00
wildrank
KEYLOGGER
|
Comments
Posted by
wildrank
on
Thursday, June 06, 2013
Are you looking for the Best Remote password hacking software or Undectable Keylogger? Do you need to spy on your remote computer without the need for physical access? or Do you wants to hack your boyfriend, girlfriend, employee email account password and also wants to monitor his/her computer. If yes then you are at right place, Today in this article I am going to write review on one of the best remote password hacking software called Sniperspy Keylogger which is almost 99% undectable.

Filed Under: KEYLOGGER
Wednesday, June 5, 2013
How to Set Up Port Forwarding on a Router
How to Set Up Port Forwarding on a Router
2013-06-05T03:54:00-07:00
wildrank
RATS
|
Comments
Posted by
wildrank
on
Wednesday, June 05, 2013
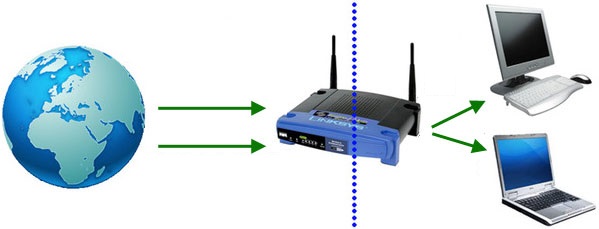
Port forwarding is the redirecting of computer signals to follow specific electronic paths into your computer. Port forwarding, also known as tunneling, is basically forwarding a network port from one node to the other. This forwarding technique allows an outside user to access a certain port (in a LAN) through a NAT (network address translation) enabled router.
Filed Under: RATS
Thursday, May 30, 2013
How To Hack Windows XP, 7, 8 Administrator Passwords In Plain Text
How To Hack Windows XP, 7, 8 Administrator Passwords In Plain Text
2013-05-30T10:59:00-07:00
wildrank
MISCELLANEOUS
|
Comments
Posted by
wildrank
on
Thursday, May 30, 2013

One more tutorial to hack Windows XP, 7, 8 passwords in plain text form. In this tutorial will show you how to hack Windows XP, 7, 8 administrator password or administrator privileges at times when you forget administrator password or when you want to gain access to a computer for which you do not know the password.
Most of us have experienced a situation where in we need to gain access to a computer which is mostly password protected or at times we may forget the administrator password without which it becomes impossible to log in to the computer. So, if you are somewhat in a same kind of situation, here is an excellent hack using which you can reset the password or make the password empty (remove the password) so that you can gain administrator access to the computer.
Filed Under: MISCELLANEOUS
Tuesday, May 28, 2013
How To Setup Darkcomet RAT With nVpn - Portforwading
How To Setup Darkcomet RAT With nVpn - Portforwading
2013-05-28T12:12:00-07:00
wildrank
RATS
|
Comments
Posted by
wildrank
on
Tuesday, May 28, 2013
Before few days I published article on How To Setup DarkComet v5.3 RAT. Today in this article I am going to explain you "How to connect to Darkcomet via nVPN". Basically DarkComet Remote Administration Tool is designed to control in the best condition and confort possible any kind of Microsoft Windows machine since Windows 2000. This DarkComet Remote Administration Tool software allow you to make hundreds of functions stealthly and remotely without any kind of autorisation in the remote process. Using Darkcomet you can easily hack any computer which is connected to internet anywhere in the world. It also helps to hack or steal your victim accounts password.


Filed Under: RATS
Saturday, May 25, 2013
Learn How To Hack Remote Computer | Hack Facebook Twitter Password Using DarkComet v5.3
Learn How To Hack Remote Computer | Hack Facebook Twitter Password Using DarkComet v5.3
2013-05-25T12:59:00-07:00
wildrank
hack facebook
|
RATS
|
Comments
Posted by
wildrank
on
Saturday, May 25, 2013

DarkComet v5.3, a Remote Administration Tool (RAT) already chosen by hundreds of thousands of peoples all over world. On WildHacker I have already written article on DarkComet v4.0 Remote Administration Tool (RAT). DarkComet Remote Administration Tool is basically designed to control in the best condition and confort possible any kind of Microsoft Windows machine since Windows 2000. This DarkComet Remote Administration Tool software allow you to make hundreds of functions stealthly and remotely without any kind of autorisation in the remote process. DarkComet is totally free software which you can use to hack and remotely control any computer in which the world which is connected to the internet without informing your victim.
Filed Under: hack facebook , RATS
Tuesday, May 21, 2013
Hack Password : Fake Mailer to send anonymous Email
Hack Password : Fake Mailer to send anonymous Email
2013-05-21T10:12:00-07:00
wildrank
KEYLOGGER
|
Phishing
|
Comments
Posted by
wildrank
on
Tuesday, May 21, 2013
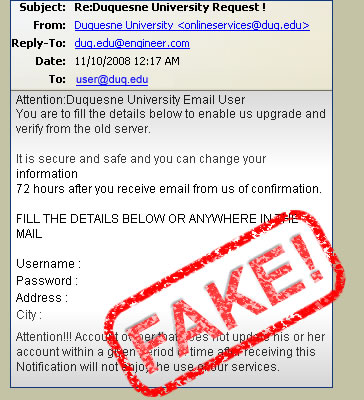
Hi everyone today in this article I am going to teach you how to send fake email. So what is fake email?? fake email is like sending email / mail to anyone, using anyone email id as sender. In such fake email you can use any information which you wants like sender, reciever, forward, subject and title anything you wants.The most reason to send fake email is a that you can use fake email for hacking password by using phishing site. You can also used fake email to steal others information or to send keylogger, rats server file to your victim. Bellow in this article I have explained step by step instruction for - how to send anonymous / fake email to your victim.
Filed Under: KEYLOGGER , Phishing
Thursday, May 16, 2013
How To Turn Your Computer Webcam Into a Spy Cam For Free Monitor
How To Turn Your Computer Webcam Into a Spy Cam For Free Monitor
2013-05-16T12:19:00-07:00
wildrank
REMOTE HACKING
|
Comments
Posted by
wildrank
on
Thursday, May 16, 2013

Do you want to know what’s going on in front of your computer or in your room while you are away? Are you suspicious that someone might be going through your personal stuff when you are away from your laptop or computer? Here is the solution for you and its totally free, no need to pay money. You can now easily monitor your computer room, office or workplace for activities going on during your absence. This can be really best way to monitor your children or even catch a cheating spouse red handed! For this, all you need is a computer with an Internet connection and a webcam attached to it.
The site called UGOlog provides a free solution to simply conver your computer or laptop webcam into a powerful spy web-camera. It’s an online web camera monitoring system with the help of which you can monitor children or cheating spouse over the internet for free. Once you’ve created your account, you can take up a quick tour and browse through the configuration guide to begin using the service.
Filed Under: REMOTE HACKING
Saturday, May 11, 2013
Learn How To Hack Computer | Hack Password | Hack Facebook | Hack Hotmail | Hack WhatsApp
Learn How To Hack Computer | Hack Password | Hack Facebook | Hack Hotmail | Hack WhatsApp
2013-05-11T11:51:00-07:00
wildrank
RATS
|
Comments
Posted by
wildrank
on
Saturday, May 11, 2013

Today going to share one more hacking tool called Apocalypse RAT which you can used to hack any computer in the world which is connected to internet. This Apocalypse RAT can also help you to hack password of any account like Facebook, Hotmail, Gmail, Twitter and many more accounts passwords of your victim accounts. As this is RAT tool which is also called as Remote Administration Tool, specially used to hack computer remotely. It is mostly used for malicious purposes, such as controlling PC’s, stealing victims information or data, deleting or editing some files in victim computer.
Filed Under: RATS
Friday, May 10, 2013
How To Get Thousands Of FB/Twitter/Youtubbe Followers Every Hour
How To Get Thousands Of FB/Twitter/Youtubbe Followers Every Hour
2013-05-10T11:56:00-07:00
wildrank
hack facebook
|
hack twitter
|
Comments
Posted by
wildrank
on
Friday, May 10, 2013
The world popular social networking site Facebook, Twitter, Youtube are great places to advertise websites or products.
Facebook, Twitter, Youtube are undoubtedly the best social network sites which if uses wisely can gift you thousands of daily readers and customers to your product or services. Such sites will surely help your brand to grow strongly on Internet / Social Media Marketing. You just need to share your products updates there and your fans, who liked you will get instant update. But if you dont have followrs on such website then these sites are useless for you.
The more Like you get, that much effectively you can drive Facebook,Twitter, Youtube visitors. As whenever you post any update on your Twitter, Youtube Fan Page, It will be visible on all the Twitter, Youtube users’ who have liked your fan page. It will not only visible to them but even their Twitter, Youtube friends can also see your updates.
Filed Under: hack facebook , hack twitter
Saturday, May 4, 2013
Hack Hotmail Password Using FUD / Undectable Sniper Spy MAC Keylogger 2013
Hack Hotmail Password Using FUD / Undectable Sniper Spy MAC Keylogger 2013
2013-05-04T11:55:00-07:00
wildrank
hack hotmail
|
Comments
Posted by
wildrank
on
Saturday, May 04, 2013
Are you worried how others might use your Mac OS X computer? Expose the truth behind the lies! SniperSpy is the only software that allows you to secretly watch your Macintosh like a television! Login from ANYWHERE using another computer, smartphone or iPad. After you install this program to the Mac you wish to monitor, it begins silently recording everything they do online. The program then uploads user activities and sends the data to your online account. You login to your account SECURELY to view logs using your own password-protected login. View the screen LIVE and see everything they do online in real time! Browse the file system, view chats, websites, keystrokes and more, with screenshots. You can also access the LIVE control panel within your secure online account to perform live monitoring functions.
Filed Under: hack hotmail
Subscribe to:
Comments
(
Atom
)