Today in this post will show you how to hack Windows administrator password or administrator privileges at times when you forget administrator password or when you want to gain access to a computer for which you do not know the password.
Most of us have experienced a situation where in we need to gain access to a computer which is mostly password protected or at times we may forget the administrator password without which it becomes impossible to log in to the computer. So, if you are somewhat in a same kind of situation, here is an excellent hack using which you can reset the password or make the password empty (remove the password) so that you can gain administrator access to the computer.
How to Hack Administrator Password | Privileges
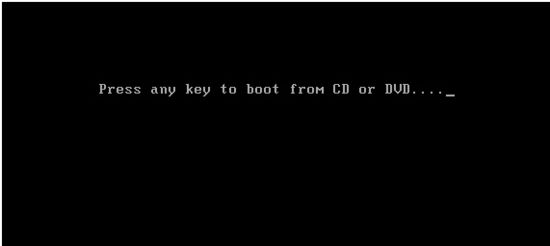
Step 1: First boot the system from the CD.
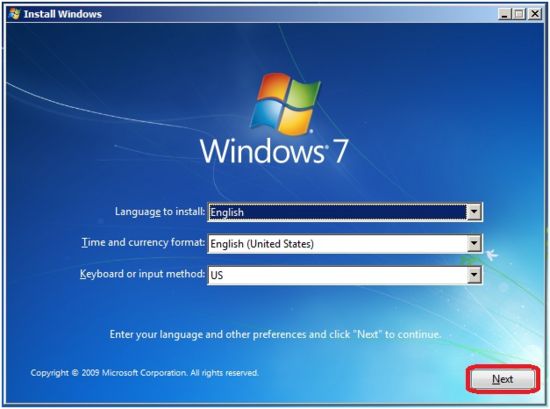
Step 2: Now press any key to boot from cd / DVD. You ll get following Install Windows Screen, now select your language and preferences and click Next to continue.
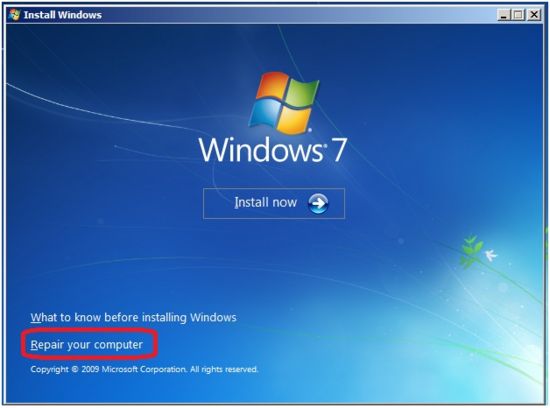
Step 3: Now choose “Repair your computer” option.
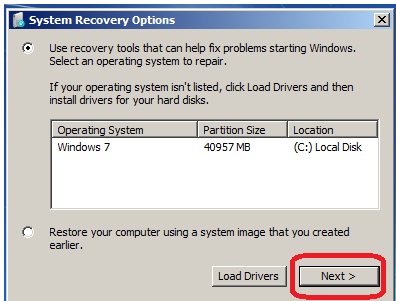
Step 4: In the System Recovery window select first option and click Next.
Step 5: Now in next window choose the Command Prompt option below.
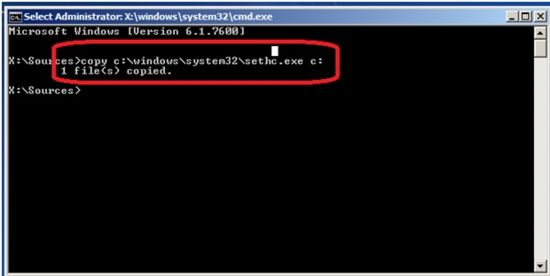
Step 6: Now in the command prompt window, copy the sethc file to C drive using the following command.
command : “ Copy C:\windows\system32\sethc.exe c: ”
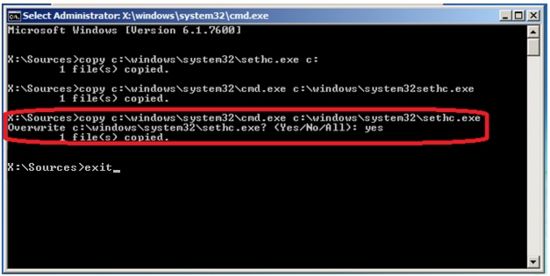
Step 7: Now replace the sethc.exe file with cmd.exe file using the following command. And type “yes” to replace the file.
Command : " Copy c:\windows\system32\cmd.exe c:\windows\syetem32\sethc.exe "
Step 8: Type "exit” command to restart the Windows setup.
Step 9: After restart, press the shift key 5 times, rapidly, when you are in the username screen. In the Sticky Keys window, click Yes.
Step 10: Now in the command prompt window type the command “net user”, “user name” and “password”.
Example : net user administrator 12345
Thats it...now you have sucessfully hack the Administrator privileges.
So, in this way you can reset the password of any Windows account at times when you forget it so that you need not re-install your OS for any reason. I hope this helps.





 If you enjoyed this post and wish to be informed whenever a new post is published, then make sure you subscribe to my regular Email Updates.
Subscribe Now!
If you enjoyed this post and wish to be informed whenever a new post is published, then make sure you subscribe to my regular Email Updates.
Subscribe Now!










